Doppleganger Sites- How AI Phishing Has Taken The Online World By Storm
February 21, 2025
In the evolving landscape of cybersecurity, a new threat has emerged that's more sophisticated and dangerous than anything we've seen before: AI-powered phishing attacks. These aren't your grandmother's obvious scam emails anymore – they're highly personalized, incredibly convincing, and nearly impossible to detect with the naked eye.
There is a very real possibility that you have either seen, or even clicked, on more than a few of these links in the last few months. According to the FBI, there has never been a more dangerous time to be clicking on links than right now. They have advised users: "do not click anything."
In this article we explore the stats and the techniques used by hackers to deliver these extremely enticing links, and how you can stay safe while browsing online.
The Rising Tide of AI Phishing
The statistics are alarming. Below you can see the data from a recent study by HoxHunt:
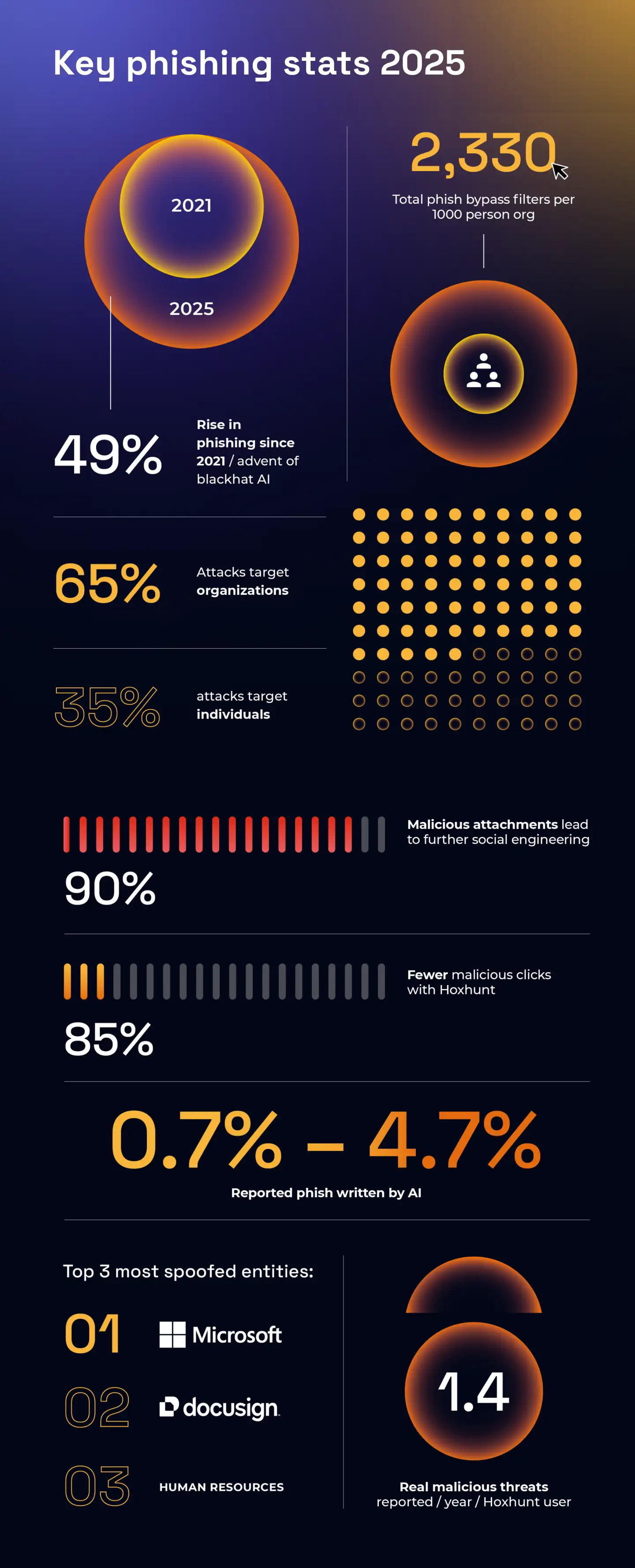
The alarming number there is 35% targeting personal users. The age old excuse of "I'm not important enough" doesn't matter to hackers apparently.
Taking this approach and coupling it with AI has allowed hackers to speed up their process and clean up a lot of their capabiltiies. Emails, texts, phone calls, and the videos on social media can all be crafted by the click of a button. They can change the voice, update the word choice, and craft a tone that matches a friend or neighbor.
But these aren't just numbers – they represent the real lives of people who are going to be disurpted by sophisticated cyber actors online.
Why AI Makes Phishing More Dangerous Than Ever
Traditional phishing attacks were often easy to spot: poor grammar, generic greetings, and obvious scam attempts. AI has changed everything. Modern AI-powered attacks can:
- Generate perfectly written emails that match your organization's tone and style
- Create convincing fake websites that are pixel-perfect copies of legitimate ones
- Analyze your social media presence to craft highly personalized messages
- Adapt and evolve their tactics in real-time based on user responses
The most frightening part? These attacks are becoming more sophisticated every day as AI technology continues to advance.
The Human Cost: Beyond the Numbers
A great example is that of Zach Latta, who posted to GitHub about his recent run in with AI phishing back in January.
Zach stated that "Someone just tried the most sophisticated phishing attack I've ever seen. I almost fell for it. My mind is a little blown."
The shocking story began with a phone call to Zach's phone, from a Google number with a normal sounding "engineer" who claimed that his account had been compromised and they wanted to let him know.
The key details from this attack were that the domain in the support email they sent him while on the call was linked to Google (g.co) and that the phone call was listed under Google (using Google Assistant). Being that Zach is very technical, he was able to stop this attack before it started.
But had it been you, would you be able to figure out that it was a very sophisticated AI phishing attempt? Or would you have clicked the link they texted directly to him while on the phone?
Why Traditional Solutions Aren't Enough
Standard anti-phishing tools rely on known threat databases and basic pattern matching. But AI-powered attacks are dynamic, constantly changing, and can bypass these traditional defenses. By the time a threat is identified and added to a database, the AI has already moved on to new variations.
Almost all security tools that exist today only protect the user after a user has clicked on a link, given it prompts a download or it brings them to a malware hosted site. What these don't account for are the types of sophisticated attacks that AI is generating today. It is capable of creating mirror images of well known sites, which can cause the user to "log in" to what they think is instagram or tiktok and end up giving their credentials to a hacker.
If the domain is newly registered or if it hasn't been added to a phishing database, these traditional tools are incapable of protecting the user from AI generated webpages.
Protecting Yourself in the AI Age
Now you're probably wondering: what on Earth can I do to protect myself or my loved ones from these sophisticated AI attacks?
What process or tool would be able to protect me while I'm browsing online?
This is where RedPhish comes in. Unlike traditional security tools that only warn you after you've clicked on a threat, RedPhish analyzes and blocks malicious content before it even loads in your browser.
This is revolutionary because it exists inside of the browser, which no other security tool does. RedPhish can scan every link before a page loads and if they are associated with phishing, malware, or ransomware it automatically removes it from the page.
In Zach's case above, it would have removed the link from from his email directly in the browser and would have notified him with an Unsafe badge. This is the magic that RedPhish is capable of.
If you have any doubt in your ability to identify a phishing attempt or that you might be getting hacked, you should seriously consider giving RedPhish a try. There are free trials available, and it could be the one thing that stops the next attack from happening.
